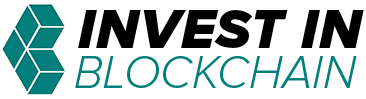In 2018, hacking will account for nearly $1 trillion in financial losses across the globe. It will affect countless industries, including banking, finance, law, insurance, healthcare, transportation, media, government and more.
Keeping data secure has become such a big problem that for every $1 spent on cloud storage, $4 is being spent on cyber-security to protect that storage. But it gets worse. For every $1 spent on cyber-security, more than $6 is still being lost to cybercrime.
This is good news for computer science majors around the world who will be able to find high-paying jobs in the cyber security industry when they join the workforce. It also bodes well for cyber security investors.
For everyone else, though, this illustrates the ineffectiveness and economic inefficiency of modern security technology and strategies. Simply put, the cyber security economy, which is valued at more than $100 billion, is broken.
Existing Cloud Storage and Enterprise Security Solutions
It’s becoming increasingly common for enterprises to store their confidential data online through cloud storage service providers. Cloud storage and cloud-based applications help businesses to reduce operational costs as well as eliminate upfront costs for hardware purchases, while also improving employee mobility. There’s a lot to love about the cloud.
Unfortunately, these advantages don’t come without costs. In the case of cloud storage, the cost for consumers is paying high premiums for enterprise-class security, which remains an imperfect solution that leaves them vulnerable to various types of security breaches.
It’s not just a select few players that are at risk, either. Every single existing cloud storage and enterprise security solution is fundamentally flawed. That’s because all of them share similar centralized design architecture, which presents several vulnerabilities:
- External threats from syndicated hacker groups
- Viral threats from malicious software programs (i.e. viruses, malware, ransomware)
- Operational failure threats and DDoS (Distributed Denial of Service) attacks
- Internal threats from bad actors, disgruntled employees
- Surveillance intercept threats or man-in-the-middle attacks
Of course, there are measures individuals and businesses can take to reduce their vulnerability. At scale, they involve expensive combinations of tools such as anti-virus and spyware software, encryption, firewalls and partitions, Multi-Factor Authorization (MFA), Data Leak Prevention (DLP) and Threat Analysis products, plus Cloud Access Security Brokers (CASBs) or Cloud Security Gateways (CSGs).
Ultimately, however, all these measures fall well short of completely protecting data stored on the cloud.
Cryptyk’s Hybrid Blockchain Solution
More than 4,500 cryptocurrencies have been created since Bitcoin launched less than a decade ago. With hype taking off and money flooding the crypto market, entrepreneurs and opportunists everywhere have been creating blockchain solutions for nonexistent or inconsequential problems. As an investor, you can narrow down the field drastically just by focusing your attention on the projects that address real, significant problems.
On that note, it’s also important for investors to understand a key difference between utility and security tokens. While public opinion is the determining factor in the value of a security token, utility tokens can develop intrinsic value as the economies that use them grow.
That brings us to Cryptyk (CTK) – a hybrid blockchain solution for enterprise security and cloud storage. Through the Cryptyk platform, Cryptyk Inc. takes a novel approach to address the vulnerabilities of modern cyber security technology and strategies.
The blockchain is categorized as a ‘hybrid’ because it combines two different decentralized platforms – multi-cloud storage and blockchain auditing.
VAULT – Decentralized Multi-Cloud Storage and File Sharing
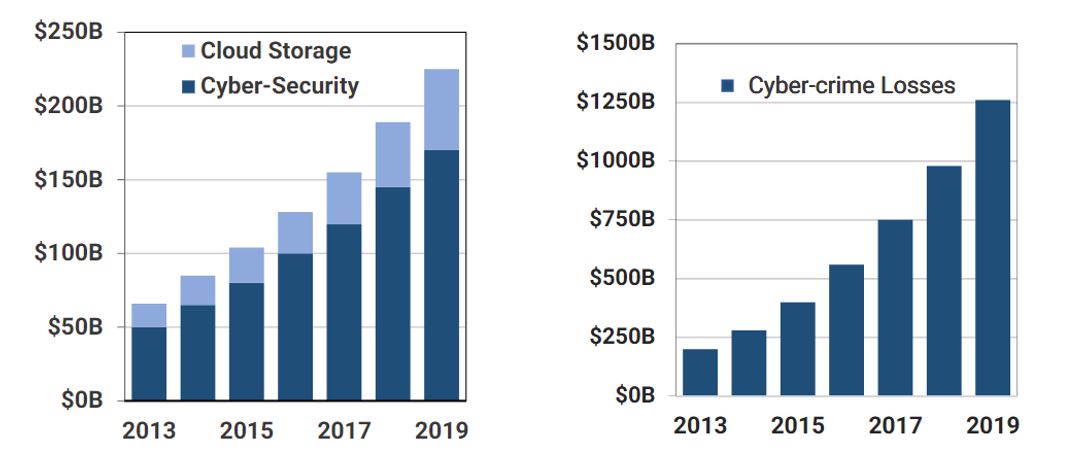
As long as hacking is extremely profitable, frequent security breaches are practically unavoidable. Realizing this, Cryptyk has created a decentralized multi-cloud storage platform that is safe-to-hack. This innovation represents a potential paradigm shift for online security.
Now, instead of playing the cat-and-mouse game with hackers who are always one step ahead of the cyber security solutions meant to stop them, Cryptyk turns the game on its head. They assume that it’s just a matter of time before hackers and viral attacks will exploit a vulnerability somewhere.
Rather than trying to prevent the inevitable, they developed a technological process that renders the exploits of security breaches useless.
When a file is uploaded to VAULT, it is automatically divided into multiple encrypted pieces that are stored separately by independent cloud storage providers such as Google Drive, Amazon S3, iCloud, Microsoft Azure, Dropbox, etc. The encryption keys that unlock access to each piece of the file are stored on the user’s own smart devices.
For a hacker to gain access to a single file, they would have to simultaneously break into 3 of the 5 storage providers, discover the uniquely coded hash that links each part of the file, decrypt 6 levels of SHA 256 bit military-grade encryption, and break into the user’s device to decrypt their private key. To put it another way, hacking is neither practical nor viable.
This process reduces the potential attack surface by more than 90%, while still enabling customers to access files with speeds comparable to Google Drive.
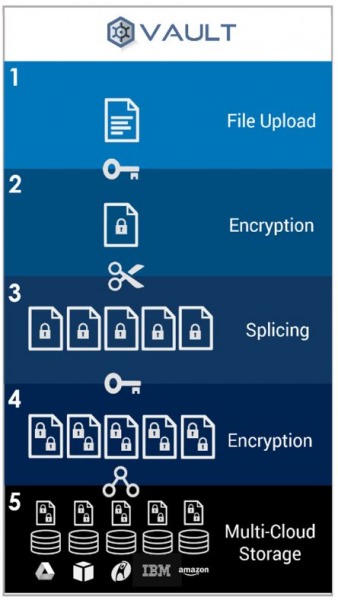
SENTRY – Blockchain Security Auditing
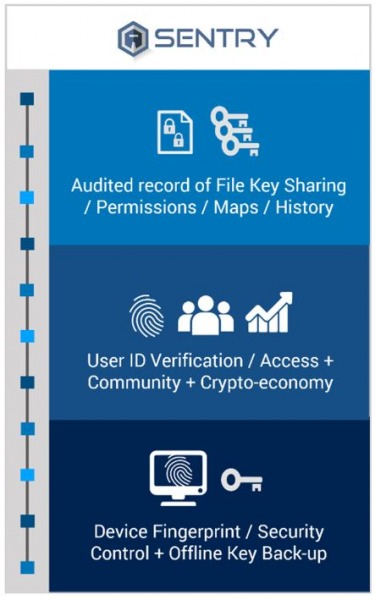
VAULT is immune to 3 of the 5 threats to cloud storage: external threats, operational threats, and viral threats. The second part of the Cryptyk hybrid solution, SENTRY, addresses the other two threats.
SENTRY is an auditing platform built on an immutable blockchain. It controls all user access to the Cryptyk platform and tracks file sharing and communications. Through continuous AI monitoring of the blockchain, Cryptyk is also able to counter internal security and surveillance threats – combining with VAULT to address all 5 of the major vulnerabilities of centralized platforms.
In addition to these security benefits, the SENTRY blockchain is also the backbone of Cryptyk’s CTK token ecosystem. It will manage activities including customer trials and purchases, mining payments, developer payments, strategic partner payments, and token exchanges with other cryptocurrencies as well as fiat currencies.
Cryptyk is built for rapid, viral growth once launched. If, for example, a bank begins using Cryptyk to store important data and documents, the customers of that bank will automatically interface through a Cryptyk account to access their bank account, legal documents, etc. This creates end-to-end security while also rapidly converting customers into investors and evangelists, as bringing in more enterprise customers will increase the value of the CTK token.
Dropbox similarly used growth hacking strategies to carve out its piece of the cloud storage market in the company’s early stages, with great success. Considering that Cryptyk has all of these tools at its disposal before even accounting for the biggest tool of all, the CTK token, the platform has a great chance to achieve significant adoption — and quickly at that.
What’s been described in this article is only scratching the surface of all the functionalities provided by the Cryptyk platform. For a full breakdown of the impressive technology and system architecture, you can read their technical whitepaper.
Current Progress and ICO Details
Cryptyk currently has a fully functioning prototype platform that was tested by 40 users and 40 hackers for 3 months. The testing proved the efficacy of the platform and provided valuable customer feedback that will be used to improve the final product design.
CTK token investors will have the ability to activate their free 2GB storage account on the prototype platform as soon as CTK tokens are distributed. These accounts will automatically be upgraded to the final product once it’s deployed.
The Cryptyk ICO has received extremely positive feedback from a number of ICO ranking and research platforms, which can be found in the Awards, Ratings & Reviews section of the project’s ICO website.
Cryptyk is an official IBM Embedded Solutions Partner and was named one of the Top 10 Enterprise Security Startups of 2018. All things considered, it’s a low-risk investment opportunity with massive potential given the market trends in cloud storage and cyber-security.
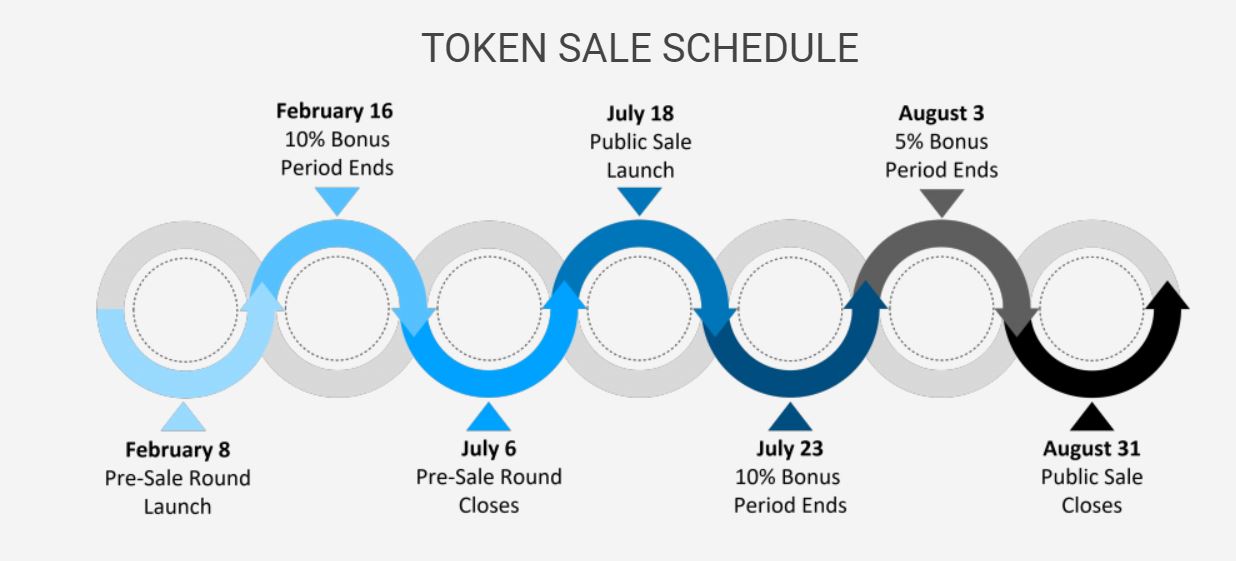
The ICO is currently in the presale round, which is discounted by 20%. Participation in the presale is limited to accredited investors only and KYC verification is required. The public sale will launch on July 18, 2018 and will be open to all non-accredited investors outside the US and Canada.
The minimum investment for the public sale is US$500. To participate, simply register on the CTK Web Wallet website.
For more information about Cryptyk, you can read their business whitepaper and FAQ. To keep up with the latest platform developments and events in the cloud storage and cyber security worlds, join Cryptyk on Telegram.