The number of digital data breaches in the U.S. has doubled since 2015. Most of these are the result of cyber attacks targeting centralized servers that hold millions of confidential records. Enterprise-level organizations are struggling to keep data secure, but as the successful hacks continue to demonstrate, traditional efforts aren’t effective enough.
Cryptyk has a promising solution to the problem of secure cloud storage. Instead of trying to prevent cyber attacks, Cryptyk renders them obsolete by encrypting, splitting, and storing file shards in multiple locations using a secure decentralized platform. The team calls it “passive immunity”, and it makes data breaches of any scale both impractical and unprofitable for hackers.
Cryptyk’s Secure Ecosystem
The global cyber-security industry is worth over $100 billion, yet cyber-security losses could reach $2 trillion by 2019. In 2015 IBM CEO Ginny Rometty called cyber crime the greatest threat to every company in the world. She made this statement before some of the largest hacks in history took place, including the Equifax breach and the Yahoo! hack that compromised over 3 billion records.
Cryptyk’s single-vendor decentralized data processing platform approaches secure storage from a unique angle. The 3 core pieces of the ecosystem include VAULT, SENTRY, and the platform’s utility token, CTK.
Here, we take a look at the role each one plays in Cryptyk’s ecosystem.
VAULT
The core of Cryptyk’s service is the VAULT, a decentralized, multi-cloud storage and sharing platform that provides passive immunity against data loss. For end-users it works like any other online storage system, right down to the drag and drop interface.
Underneath, however, Cryptyk leverages the blockchain to ensure data remains secure.
A stored document is encrypted the moment it interacts with Cryptyk. It’s then split into 5 shards, each of which is encrypted a second time. These pieces are sent to 5 different third-party cloud hosts, such as Amazon AWS, Dropbox, or Google Drive. Cryptyk’s SENTRY system then monitors access to these files to ensure no suspicious activity takes place.
In order to access a single file protected by VAULT, a hacker would have to simultaneously break into 3 of the 5 storage providers, locate the uniquely-coded hash that links each shard, decrypt 6 levels of SHA-256 encryption, then break into the user’s device and decrypt their private key. Gaining access to millions of files simply isn’t feasible.
 Source: cryptyk.io
Source: cryptyk.io
SENTRY
Sentry is a decentralized system for auditing and tracking sharing events to maintain permissioned control over files. It works alongside VAULT to provide monitoring and safety features that improve security by stopping suspicious activity before data is compromised.
With SENTRY active, IT departments have granular control over a wide variety of monitoring systems, everything from leak prevention to geo-fencing and user quarantining. The team can set up systems to catch bad actors and intercept threats as they occur instead of simply responding to attacks to minimize loss.
SENTRY’s API maintains security while allowing programs such as Word and Excel to interface with files stored in the VAULT. Connection latency stays below 200 ms, which allows teams to engage in real-time file editing and collaboration without exposing encrypted data. Future SENTRY developments will include Cryptyk’s decentralized mail and chat applications.
Cryptyk’s technology whitepaper provides a more detailed look at VAULT, SENTRY, and the blockchain technology that powers the entire architecture.
The Cryptyk Token (CTK)
Cryptyk’s entire cyber security ecosystem is powered by CTK. The ERC-20 token facilitates transactions on the platform, taking the place of fiat currency to allow for faster and more secure payments. CTK will be made available on several exchanges approximately one month after the public token sale concludes.
Because CTK is a utility token, it can also increase in value based on a variety of factors, the most important of which is customer adoption of the platform. Holding a valued utility token like CTK can incentivize participation from customers, developers, partners, and cryptocurrency investors alike.
The higher the demand for Cryptyk’s platform, the more affordable Cryptyk becomes for users, and the more profitable CTK is for investors.
Key Advantages of Cryptyk
Cryptyk’s VAULT and SENTRY features provide a secure core for data protection. The platform could provide inexpensive, decentralized storage for financial, legal, transport, media, healthcare, government, and related industries. Any enterprise that needs secure cloud storage will find a potential solution in Cryptyk.
Partnerships are already in place with companies like IBM, Bancor, Founder’s Credit Union, and others. Alliance partnership discussions are currently taking place with a number of large finance and legal clients, as well.
Cryptyk has zero visibility into file contents. This means neither Cryptyk Inc., the developer of the platform, nor the non-profit economic governance body Cryptyk Foundation can gain access to information that passes through the network.
At the time of writing, Cryptyk has a fully working web client prototype in place. The system was stress-tested for 3 months by 40 trial customers and over 40 hackers. The prototype features a user-friendly drag and drop web-based interface anyone can immediately start using.
It looks and feels like Dropbox or Google Drive but beneath the streamlined exterior, Cryptyk’s systems work to keep data secure.
Investing in CTK
 Source: cryptyk.io
Source: cryptyk.io
The investment value of utility tokens such as CTK is driven by customer adoption and product revenue. This is in contrast to security tokens whose price fluctuates with market sentiment and investor speculation. If the platform does well then the token’s price will rise, making them a generally stronger long-term investment.
CTK is firmly tied to the Cryptyk platform as an internal payments currency. When an enterprise purchases a subscription, for example, it can pay using fiat, BTC, or ETH. This is automatically converted into the value equivalent of CTK tokens.
If the relative price of the currency pair favors CTK, fewer tokens will be required to achieve the same results. In other words, the more valuable CTK becomes, the less transactions will cost as compared to fiat.
Estimates suggest utility tokens such as CTK carry a 2-3 year ROI potential of 50 to 100 times the original price. CTK’s cost will start low and be tied to the cryptocurrency market at first.
Customer trials will begin in Q1 2019, at which point the value will be synchronous with the platform’s revenue and performance. By 2021, the Cryptyk platform’s annual revenues are expected to reach $240 million.
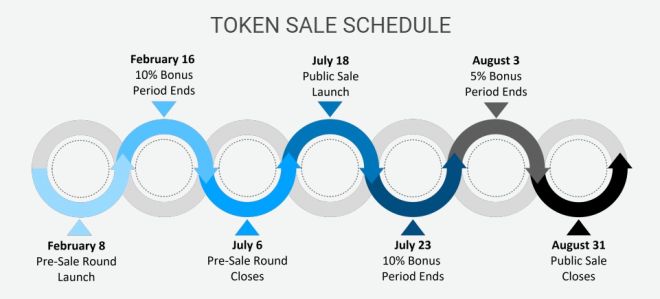
The CTK economy launched via a token sale event in February 2018. The presale round closes July 6, 2018 with a public sale launch set for July 18. Token sale bonuses expire on August 3, and all public sales will close on August 31, 2018.
For more details about the ICO event, see Cryptyk’s business whitepaper.
Final Thoughts
Cryptyk has identified a stress point for enterprise organizations and is aiming for a unique and affordable solution. Delivering decentralized “passive immunity” against cyber attacks could transform how enterprises interact with data, cutting out expensive and ineffective methods in favor of a fast, easy to use, and secure decentralized platform.
The CTK utility token is a promising concept for investors, as well. With token price tied directly to the platform’s success, CTK could experience a gradual rise to high long-term value.
Learn more about the Cryptyk platform and the token sale on the official website.
Related: Cryptyk: How Decentralization Can Improve Cyber Security and Cloud Storage