If you haven’t heard the most recent buzz in the crypto-sphere over the last week, then you’re probably living under a rock, because it’s (unfortunately) all people have been focusing on. At around 4am EST on April 16, 2018, mid livestream, cryptocurrency investor, advisor, and self-proclaimed “evangelist,” Ian Balina had just shy of US$2 million stolen from his ETH wallet.
He abruptly ended his livestream, tweeting the following message –
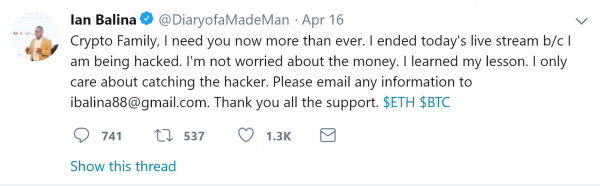
It’s hard to fathom how someone with holdings in the millions stored it so recklessly. And the scariest part – it’s more common than you think. In a now-deleted Telegram massage, Balina explained how he thinks he was hacked:
This is how I think I got hacked. My college email was listed as a recovery email to my Gmail. I remember getting an email about it being compromised, and tried to follow up with my college security to get it resolved, but wasn’t able to get it handled in [sic] fast manner and gave up on it thinking it was just an old email.
I keep text versions of my private keys stored in my Evernote, as encrypted text files with passwords. I think they hacked my email using my college email and then hacked my Evernote.
For those not exactly sure who Ian Balina is, he started making YouTube videos in early 2017 teaching investors how to “hack the system” and earn a six-figure income. He only rose to prominence in the last six months after his revelation that he parlayed a $90,000 investment into $4 million in less than 12 months – a statement that he corroborated with his Blockfolio snapshots posted on Twitter.
Like him or not, the Ian Balina hack is an expensive lesson on how important it is to keep your crypto secure. Here are 4 fundamental security takeaways and reminders HODLers should familiarize themselves with and implement into their crypto browsing, investing, and storage in order to minimize the chances of being hacked (or being lambasted on social media).
1. Don’t Flaunt It Just Because You Got It
Just as the average person doesn’t walk around yelling out their bank account details and how much money they have in their wallet in a seedy neighborhood at 2 a.m., crypto investors shouldn’t be publicizing their crypto portfolio and holdings online – or in person.
Even when engaging in popular online forums, such as BitcoinTalk or Reddit, discretion is key – just ask this Redditor who actually posted their Siacoin private seed online and was given a lesson in security by a luckily-friendly fellow Redditor.
Refraining from broadcasting financial information online seems like an obvious tip, but it still bears repeating.
Here’s just a few of the consequences and security risks it opens investors up to:
- Targeted phishing scams
- Ransomware
- Social engineering
- Robbery
That’s right, robbery. Take it from this Taiwanese man who showed proof of his bitcoins to 3 scammers, and was ultimately assaulted and robbed. The scammers transfered 18 bitcoins – estimated at over US$170,000 – out of his account (via phone).
Even the Prime Minister of Iceland ended up as an unwitting bystander to the escape of a man suspected of stealing around 600 computers with Bitcoin, in what’s considered Iceland’s biggest-ever robbery.
You may not want to be overlooked, but you also don’t want to be looked over too much. Don’t dox yourself.
2. Use Cold Storage if You’re Storing More Than 1 Month’s Salary Online
When deciding whether to pony up and spend $60-$150 on a hardware wallet, HODLers should ask themselves how much they are okay with losing, should their passwords or login information become compromised.
Storing private keys online and using hot wallets is manageable and appropriate for investors storing small sums online, while cold storage – the storage of funds in an offline device – and hardware wallets should be used by investors holding over one month’s salary on an exchange.
However, if even losing a week’s salary to a hack would drastically affect you – financially or emotionally – then it’s worth spending that weekend’s bar tab or some of the money saved up for your nana’s surprise 90th birthday.
Where Balina erred in his storage and/or private keys was through his use of a generic and free cloud storage program and compromised college email, which enabled hackers to hack his current email and gain access to Evernote.
Storing a private key or seed online is not considered cold storage – it’s then considered a hot wallet, as it’s connected to the internet – and comes with the numerous issues and security vulnerabilities associated with hot wallets.
If in doubt, go cold.
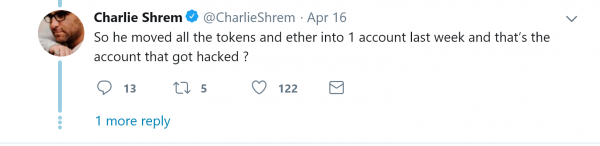
Both Trezor and the Ledger Nano are two popular and reputable hardware wallets for storing funds. Just remember, a small investment in security now could prevent Charlie Shrem – a founding member of the Bitcoin Foundation – from giving you the once over in the future.
And, if you’re looking for mobility mixed in with cold storage, consider using the CoolWallet S, a mobile hardware wallet which supports Bitcoin, Ethereum, Ripple, Litecoin, and Bitcoin Cash (ERC-20 tokens forthcoming).
Additionally, paper wallets are an effective means of cold storage, provided you don’t place the piece of paper with your recovery seed and PIN under your daughter’s pillow before a flight and hire a cleaning team to tidy up.
For a comprehensive look at cryptocurrency wallets, check out our beginner’s guide to cryptocurrency wallets.
3. Beware of Punycode
Ever since crypto’s meteoric rise in the last few years, phishing has become the preferred method for scammers looking to take advantage of careless HODLers and those quick to jump on free crypto giveaways – thanks @VitarikBooterun from Russia who has 2 followers and no profile picture (this is a fake and completely made up Twitter handle, but log in to Twitter, find a @VitalikButerin Tweet and take note).
The most worrying issue surrounding present-day phishing attacks is their complexity and aesthetic authenticity. Especially for people like me, someone who’s technically supposed to wear reading glasses but is unconvinced by his mother telling him he looks more handsome with them on – and instead opts for squinting and holding the computer close to his face.
And, I’m not the only one who has been fooled before.
Earlier this year, it came to light that a fake Tron account had been verified by Twitter. The account had amassed over 140,000 followers while tweeting out scam giveaways where users sent small amounts of ETH to a posted address with promise of receiving 10x that in return.
It doesn’t stop there. Phishing attacks are getting more creative. Although not used in the Balina hack, this phishing method is worth keeping an eye on: look no further than “punycode.”

Simply put, punycode is a special representation of Unicode, allowing hackers to convert characters to ASCII, a smaller and restricted character set – think of the German language. For example, the German name for Munich is ‘München’.
So, how do you tell legitimate websites from malicious ones?
- For starters, look for the green ‘https’ and word ‘Secure’ to the direct left of a website’s URL address. Green indicates the website has obtained the necessary SSL certificates and is legitimate.
- Secondly, bookmarking a frequently visited webpage is an effective means of minimizing error or misspelling.
- Double check to make sure the URL was entered correctly, and trust your gut. A website displaying pop-ups upon immediately landing on the page probably isn’t the correct site to trade and store thousands of dollars worth of crypto.
4. Two-Factor Authentication is Key – One Method Reigns Supreme
Backing up crypto accounts and logins with two-factor authentication – also known as 2FA – is an essential step in enhancing portfolio security. 2FA requires users to enter a one-time password (OTP) provided to them via smartphone or application, in order to complete the log-in process.
However, users taking security seriously should desist from using SMS authentication for 2FA and instead use apps such as Google Authenticator, or the less popular Authy.
Researchers and security experts have long-warned against the use of text messages as a validating security measure when logging in online, noting that hackers have previously orchestrated large-scale attacks where they exploited known flaws in various cell networks in order to intercept text messages sent to users.
The advantage of Google Authenticator is that it relies on the strength of not needing to interact with a cell carrier, keeping the time-constrained authentication codes on the app (usually for 30 seconds) and phone. Even if a hacker quickly moves a user’s phone number to a new phone, the code is unaffected.
When using Google Authenticator or other 2FA apps, it’s essential to back up private keys and store them safely – just in case you break or lose your phone.
Final Thoughts

While some in the crypto community aren’t convinced Balina was genuinely hacked – pointing out several suspicious circumstances and reasons why Balina may have actually had a direct hand in it – Balina has since refuted such claims, stating the hack is now officially under criminal investigation.
Regardless of what actually happened, it’s clear that even “seasoned” crypto holders are committing egregious and obvious security mistakes.
Hopefully this article serves as a reminder to everyone out there that it’s important to take a moment to reassess whether you are taking the proper precautionary measures – no matter how simple and basic they seem – to securely transact and store cryptocurrency.
Related: How to Secure Your Cryptocurrencies