The team behind the Trezor hardware wallet has addressed the vulnerabilities exposed by rival hardware wallet manufacturer Ledger. On March 11, Ledger released a report that detailed 5 vulnerabilities in the Trezor wallet.
Ledger has a division that focuses on finding exploits and bugs in its own and competitor’s wallets. Attack Lab, the team that found the flaws, noticed several possible attack opportunities in the Trezor wallet.
The two most notable are that the Trezor wallet can be exploited by injecting the device with malware and re-sealing it in its box. The team also guessed the PIN number of the device through a side channel attack.
The report read:
The analysis encompassed both of Trezor’s hardware wallets (Trezor One, Trezor T), focusing on the Trezor One. It also applies to clones of Trezor wallets. We responsibly disclosed these vulnerabilities to the vendor, allowing them to take appropriate measures for protecting their users.
Trezor responded almost immediately, responding the day after on March 12. The Trezor team stressed that none of the vulnerabilities discovered were exploitable remotely, and some of them have been patched.
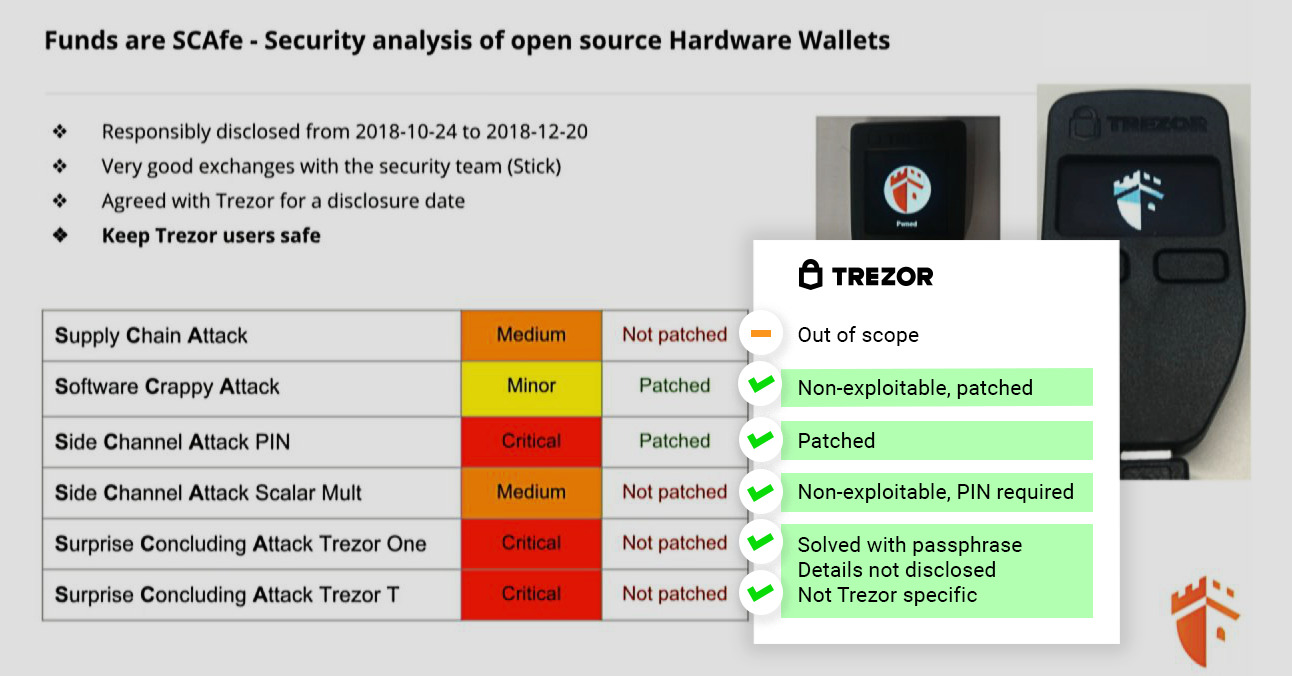
They also say that all of the attacks require physical access to the device, specialized equipment and technical expertise. Trezor refers to a survey conducted by Binance, which concluded that two-thirds of respondents perceive remote attacks as the most threatening.
Trezor concluded by saying that no wallet is 100% safe:
This whole episode is a valuable lesson for us. We need to communicate something that we already know: No hardware is unhackable, and depending on what your security model is, there are tools which you can use to mitigate threats. For users who are wary of physical attacks, passphrases for plausible deniability and operational security are the way to go. For users who are concerned about remote attacks, nothing changes.